Exploring the Persistent Cyber Threats Facing German Businesses from Foreign Actors
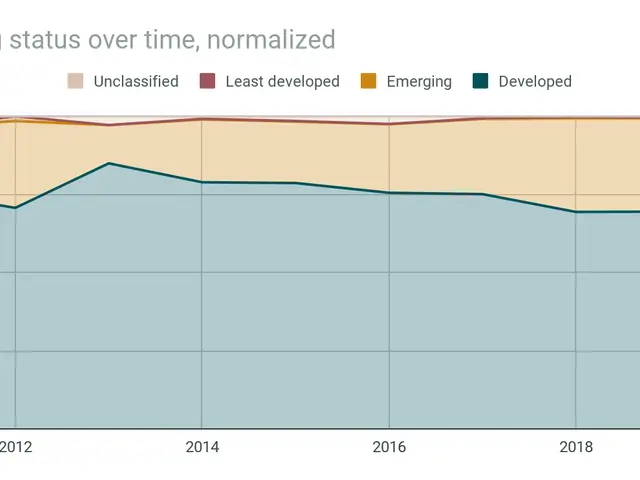
German companies have grappled with escalating financial losses due to cyberattacks, totaling approximately €267 billion annually. A report by Bitkom, published in Berlin, signaled China as the chief instigator of these digital assaults on German enterprises. In their recent survey involving over 1,000 companies across various sectors, 45% of the affected firms attributed the attacks to China (up from 42% in 2023). Traditionally, attacks originating from Russia held the top position, but this trend has dramatically shifted, with 39% of the targeted firms reporting attacks from their Eastern neighbor (down from 46% in 2023).
Experiencing turbulent times
In April 2023, media outlets reported that hackers from the People's Republic had been spying on Volkswagen for years. Their ultimate goal was the automaker's technological know-how, revealing the true extent and nature of the cyber threat Challenging times necessitate an increased awareness of the potential threats facing German businesses.
The Swiss cheese model of cybersecurity
Over a third (36%) of the targeted companies remained unaware of the attackers’ origin. Among these victims, approximately one-fifth (20%) assumed the attack originated from Germany, and a quarter suspected US-based hackers. The complexities of tracking down these criminals often impart a sense of helplessness and confusion, as attacks can originate from multiple sources. There is no one-size-fits-all approach for bolstering cyber defenses, which resemble the Swiss cheese model with layers of protection.
Understanding the threat landscape
AI playing a crucial role
Cybercriminals regularly employ artificial intelligence (AI) techniques to bolster the success rates of their hacking attacks. Utilizing deepfakes within text, images, or sound, AI enables attackers to better deceive their targets. Regrettably, one in three German companies still refrains from incorporating AI into their cybersecurity strategies, creating an insufficient defense against such modern threat vectors.
Evolving vulnerabilities
Employees’ online activities, utilizing multiple devices and applications, contribute to potential weaknesses for attackers. Misusing apps, SMS services, and social channels can inadvertently expose sensitive information. At present, the intricate online behavior of employees poses an insurmountable challenge to traditional cybersecurity strategies. The adoption of a "Zero-Trust Strategy" is recommended to mitigate the threats posed by these shifting vulnerabilities.
Critical infrastructures at risk
Agriculture, industry, and health sectors are particularly vulnerable to cyber attacks on critical infrastructure, causing significant damage and disruption. States and sophisticated cybercriminals represent the main source of these attacks, driven by strategic or financial gain.
Supply chain vulnerability
Supply chains are the new frontline in the battle against cybercriminals. Companies are deliberate targets of such attacks, aiming to steal corporate data, access credentials, customer information, and source code. In turn, these attacks can have disruptive consequences for entire sectors interconnected through supply chains.
AI fortifying security teams
The scarcity of suitably skilled cybersecurity personnel continues to impact German businesses, as companies endeavor to expand their talents pool. AI countermeasures are deployed to augment cybersecurity teams, automating routine tasks and bolstering capabilities, enabling threat detection, and analysis.
Data breach and business interruptions
Data breaches and business interruptions pose significant risks for German companies, with over 60% of executives citing data breaches as a primary concern. Despite the proliferation of sophisticated cyberattacks culminating in data breaches and business interruptions, the adoption of ransomware and cyber-extortion techniques persists.
In light of these threats, German companies need to fortify their defenses with robust cybersecurity measures, combining AI and a “Zero-Trust Strategy” of protection. Lastly, the potential impact of these attacks necessitates balanced risk assessment, recognizing the opportunities and the risks coalesced within various global partners.
Sources
- (1):
- (2):
- (3):
- (4):